Why Traditional Data Security Management Fails Enterprises and What Works Instead
Learn proven data security management strategies that eliminate breaches without stifling business agility.
Enterprise data security management has evolved far beyond perimeter defenses and access controls. As organizations embrace cloud platforms and democratize data access, traditional security approaches create dangerous gaps that expose sensitive information to both internal misuse and external threats.
Modern enterprises need comprehensive frameworks that protect data throughout its lifecycle while enabling the self-service capabilities that drive competitive advantage.
This comprehensive framework addresses the most pressing data security management challenges facing modern enterprises while enabling the self-service capabilities that drive competitive advantage.
From understanding the true cost of security failures to implementing unified governance across complex data ecosystems, we'll explore practical strategies that transform security from a business constraint into a strategic enabler.
What is data security management?
Data security management is the comprehensive discipline of protecting organizational data assets throughout their entire lifecycle while enabling authorized access across complex, distributed technology environments.
Unlike traditional IT security that focuses on perimeter defense, data security management manages the protection, governance, and controlled access of information as it flows between systems, undergoes transformation, and serves diverse business functions across global operations.
How does it differ from general cybersecurity
Data security management operates at a fundamentally different scale and complexity, most especially for enterprises, than traditional cybersecurity approaches.
While general cybersecurity focuses on protecting networks, applications, and devices, enterprise data security must safeguard information assets that flow across multiple systems, span various jurisdictions, and serve diverse business functions simultaneously.
The key distinction lies in the dynamic nature of data itself.
Unlike static infrastructure that can be secured through perimeter controls, data moves constantly between systems, gets transformed for different purposes, and must remain accessible to authorized users regardless of location or device. This dynamic nature fundamentally changes how data security must be approached.
Four critical data security management challenges facing enterprises
Despite massive investments in security technology, enterprises continue to struggle with data protection challenges that traditional approaches cannot adequately address. These challenges stem from the fundamental shift toward distributed data architectures, self-service analytics, and cloud-native platforms that render legacy security models obsolete.
The 'seven different systems' security nightmare
Enterprise data environments typically span multiple platforms, each with its own security model, access controls, and governance requirements.
This fragmentation creates what security experts describe as the seven different systems syndrome, where organizations manage separate security profiles for data warehouses, analytics platforms, cloud storage, on-premises databases, BI applications, and data catalogs.
Each system implements security differently, creating gaps between platforms that malicious actors can exploit. User access privileges that seem appropriate within individual systems become problematic when combined across the enterprise data ecosystem.
A user with read-only access to the data warehouse might have administrative privileges in the ETL platform, effectively granting them the ability to modify data despite apparent restrictions.
The administrative burden of managing multiple security systems also creates operational risks. Security teams struggle to maintain consistent policies across platforms, leading to configuration drift where initially secure systems gradually develop vulnerabilities through inconsistent maintenance.
When security incidents occur, investigations become complex puzzles as teams trace activities across disconnected audit logs and monitoring systems.
Shadow IT creating ungoverned access points
The democratization of data access has created widespread shadow data practices that bypass centralized security controls. Business users, frustrated by slow response times from central data teams, increasingly copy sensitive information to personal devices, cloud storage accounts, and desktop applications that lack appropriate security controls.
This shadow IT behavior emerges where legitimate business needs conflict with security requirements. When critical business decisions depend on data analysis but formal request processes take weeks, users inevitably find workarounds that prioritize speed over security.
These informal data copies proliferate throughout the organization, creating an invisible attack surface that security teams cannot monitor or protect.
Cloud applications compound this challenge as users can easily extract data from enterprise systems and upload it to personal Dropbox accounts, Google Drive folders, or shared collaboration platforms.
While these services may offer their own security features, they operate outside enterprise security policies and lack integration with corporate identity management systems.
Security bottlenecks that stifle business innovation
Enterprises face constant tension between security requirements and business agility. Traditional security approaches that emphasize control and restriction often conflict with the self-service data access capabilities that drive competitive advantage. Organizations struggle to enable innovation while maintaining appropriate protection for sensitive information.
This challenge becomes particularly acute with data science and analytics initiatives that require exploratory access to diverse datasets. Data scientists need freedom to experiment with different data combinations and analytical approaches, but security teams worry about inadvertent exposure of sensitive information through these experimental processes.
The approval-based security models that work for traditional IT systems become bottlenecks when applied to dynamic data workflows. Business teams that need to respond quickly to market changes cannot wait weeks for security reviews of every data access request. Yet granting broad access privileges creates risks that concern security leaders.
Cloud platform adoption amplifies these scaling challenges as organizations must balance the agility benefits of cloud services with security requirements for data protection. Teams want to leverage cloud-native capabilities for faster deployment and lower costs, but security teams need assurance that cloud configurations meet enterprise protection standards.
Fragmented regulatory requirements across global operations
Global enterprises must navigate increasingly complex regulatory landscapes where data protection requirements vary significantly by geography, industry, and data type, necessitating modern data strategies.
What constitutes adequate protection in one jurisdiction may be insufficient or excessive in another, creating compliance challenges that traditional security approaches cannot address effectively.
Data residency requirements exemplify this complexity, as regulations like GDPR in Europe and various privacy laws in different countries impose specific restrictions on where data can be stored and processed.
Enterprises must maintain detailed visibility into data locations and movements to demonstrate compliance while ensuring that business operations can continue across geographic boundaries.
Industry-specific regulations add another layer of complexity, as healthcare organizations must comply with HIPAA in the United States while also meeting GDPR requirements for European operations. Financial services firms face similar challenges with regulations like PCI-DSS, SOX, and Basel III that impose specific security requirements for different types of financial data.
How Databricks helps overcome data security management challenges facing enterprises
Databricks addresses enterprise data security management challenges through a unified platform approach that consolidates security controls while enabling the self-service capabilities modern businesses demand. Let’s see how.
Unity Catalog centralizes security without bottlenecks
Unity Catalog addresses the "seven different systems" security nightmare by providing a single, comprehensive governance layer that spans all data assets within the Databricks platform.
Rather than managing separate security policies for different tools and platforms, organizations can define access controls, audit policies, and compliance requirements once and have them enforced consistently across all data workflows.
This unified approach extends beyond simple access control to encompass comprehensive lineage tracking, which demonstrates how data flows through transformations, analyses, and reporting processes.
When security incidents occur, teams can quickly understand the scope of potential exposure by tracing data movement through complete audit trails that capture every interaction with sensitive information.
The platform implements fine-grained access controls that can restrict access at the table, column, or even row level based on user attributes and business context. This granular control enables organizations to implement sophisticated security policies that balance protection with usability, ensuring that users can access the information they need for their roles without exposing sensitive data inappropriately.
Unity Catalog also automates compliance reporting by maintaining comprehensive metadata about data usage, access patterns, and security controls. This automation dramatically reduces the effort required for regulatory audits while providing assurance that security policies are being enforced consistently across the enterprise data ecosystem.
Automated policy enforcement eliminates configuration drift
Databricks implements security policies through code rather than manual configuration, eliminating the configuration drift that plagues traditional multi-system environments. Security teams can define policies as code that gets automatically deployed and enforced across all data platforms, ensuring consistent protection regardless of how the underlying infrastructure scales or evolves.
This approach addresses a critical challenge identified in our survey, where 37% of data leaders cite consolidating data platforms as their top priority.
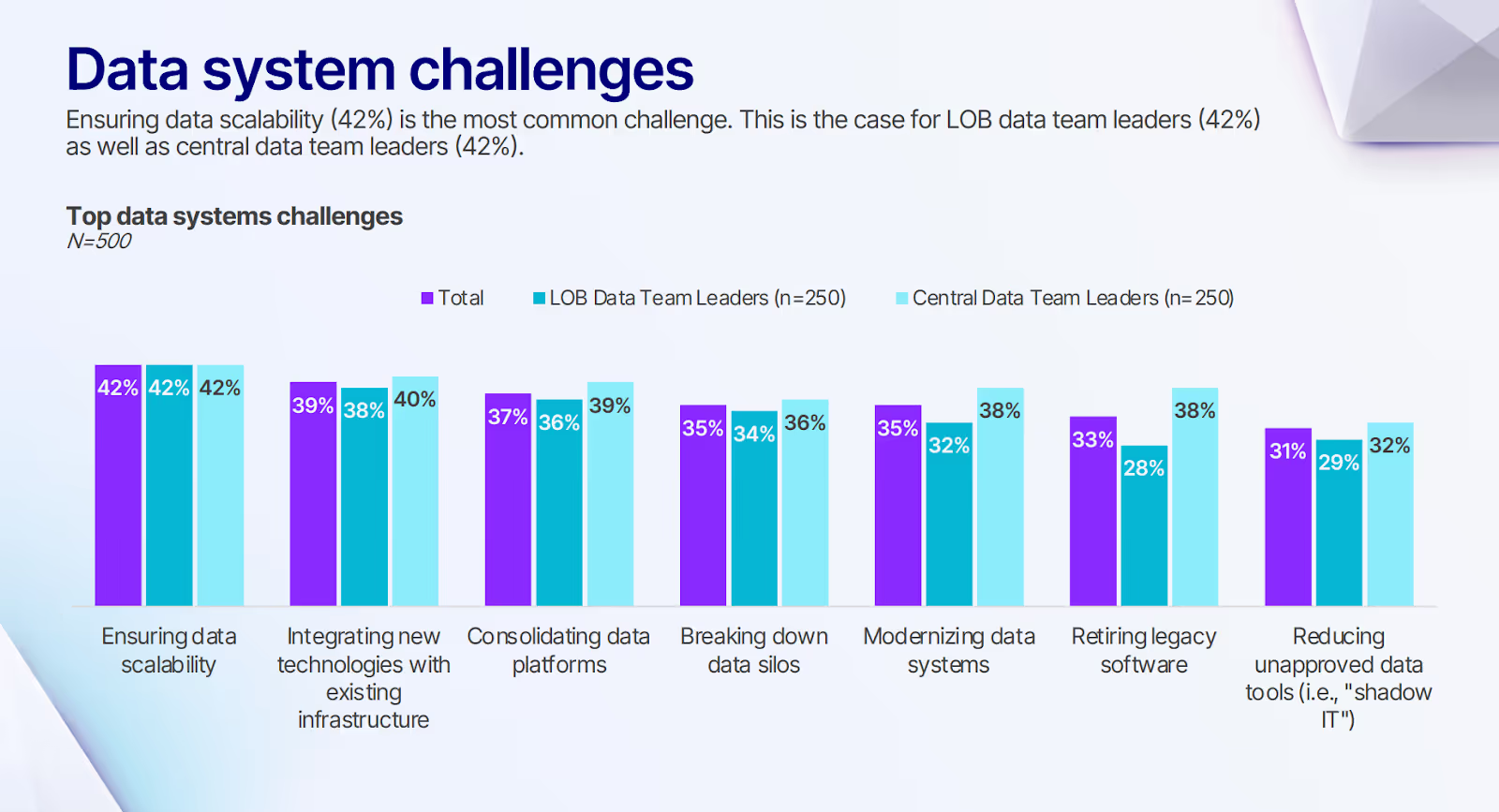
By providing a unified platform that can enforce consistent security policies automatically, Databricks helps organizations reduce the complexity that creates security vulnerabilities in fragmented environments.
The platform's automated policy enforcement extends to data classification and tagging, where sensitive information gets automatically identified and protected based on predefined rules. This automation ensures that new datasets inherit appropriate security controls from the moment they enter the platform, preventing the gaps that occur when security teams must manually review and classify every new data source.
Policy enforcement also adapts dynamically to changing business contexts, automatically applying different protection levels based on data sensitivity, user roles, and regulatory requirements. This context-aware security ensures that protection scales appropriately without creating unnecessary barriers for legitimate business use cases.
Identity integration eliminates shadow data access
Databricks integrates deeply with enterprise identity management systems, ensuring that data access privileges align with business roles and responsibilities defined in corporate directories. This integration eliminates the identity sprawl that creates security vulnerabilities when users maintain separate accounts across multiple data platforms.
The platform's identity integration extends beyond simple authentication to include comprehensive authorization policies that consider user attributes, group memberships, and business context when making access decisions.
This sophisticated approach enables organizations to implement complex security policies that adapt to changing business needs without requiring manual intervention.
By providing self-service capabilities within a governed framework, Databricks addresses the root cause of shadow data practices. Business users can access the information they need through approved channels that maintain security controls, reducing the incentive to create unauthorized data copies that bypass enterprise security policies.
The platform also implements session management and access controls that prevent data exfiltration while enabling legitimate business use. Users can analyze sensitive information within the secure platform environment without the ability to extract raw data to unsecured locations, maintaining protection while enabling innovation.
Cloud-native security scales with business growth
Databricks leverages cloud-native security capabilities that scale automatically with business growth, eliminating the capacity constraints that force organizations to choose between security and performance. The platform integrates with cloud security services to provide defense-in-depth protection that adapts to changing threat landscapes without requiring manual intervention.
This cloud-native approach includes automatic encryption for data at rest and in transit, ensuring that sensitive information remains protected throughout its lifecycle. The platform manages encryption keys securely while providing the performance necessary for large-scale analytics workloads, eliminating the traditional trade-off between security and speed.
The platform's security architecture also includes comprehensive monitoring and alerting capabilities that provide real-time visibility into potential security threats, leveraging advancements in AI in data transformation.
These capabilities leverage machine learning to identify anomalous access patterns and potential security incidents, enabling security teams to respond quickly to threats before they cause significant damage.
By providing security capabilities that scale with business needs, Databricks enables organizations to maintain protection standards while pursuing growth opportunities. This scalability ensures that security becomes an enabler of business success rather than a constraint on innovation and expansion.
Regulatory compliance built into the platform architecture
Databricks addresses regulatory compliance challenges by embedding compliance capabilities directly into the platform architecture rather than treating them as add-on features. This approach ensures that compliance requirements are met automatically through normal platform operations rather than requiring separate processes that create administrative overhead and potential gaps.
The platform maintains comprehensive audit trails that meet regulatory requirements for data governance and access control. These audit trails capture detailed information about data access, transformations, and usage patterns in formats that regulatory auditors can easily review and validate.
For organizations operating across multiple jurisdictions, Databricks provides capabilities to implement region-specific security controls and data residency requirements. The platform can automatically route data processing to appropriate geographic regions while maintaining consistent security policies across all locations.
The platform also includes built-in capabilities for data privacy and protection that help organizations comply with regulations like GDPR, CCPA, and HIPAA. These capabilities include automated data anonymization, consent management, and right-to-be-forgotten processing that reduce the compliance burden while ensuring regulatory requirements are met effectively.
Why tech capabilities alone are not enough
While Databricks provides a robust foundation for enterprise data security, organizations often struggle with the complexity of implementing comprehensive security policies across diverse data workflows.
The platform's powerful capabilities can be overwhelming for teams that need to balance security requirements with business agility, particularly when business users require self-service access to sensitive data.
The challenge intensifies when organizations attempt to migrate from legacy systems with established security practices. Teams must navigate the transition from familiar but fragmented security controls to Databricks' unified approach while maintaining business continuity and regulatory compliance.
This transition often reveals gaps in security expertise as teams adapt to cloud-native security models that differ significantly from traditional on-premises approaches.
Many enterprises also struggle with the cultural shift required to implement effective data security in collaborative environments, highlighting the need to modernize education in data engineering.
Traditional security models that emphasize restriction and control must evolve to support the self-service capabilities that drive business value, requiring security teams to think differently about risk management and access control.
Business teams need access to sensitive data for analytics and reporting, but security teams worry about inadvertent exposure through exploratory data analysis and collaborative workflows that are difficult to monitor and control effectively.
How Prophecy transforms enterprise data security management in Databricks
The gap between platform capabilities and practical implementation often leaves teams struggling to balance security requirements with the self-service access that drives business value.
Here's how Prophecy bridges these data security gaps while amplifying Databricks' native security capabilities:
- Visual pipeline development with embedded governance controls: Business users can build complex data workflows through intuitive drag-and-drop interfaces while Prophecy automatically enforces security policies defined in Unity Catalog.
- Automated security-compliant code generation: Every visual pipeline automatically generates high-quality code that follows enterprise security best practices and integrates seamlessly with Databricks security frameworks.
- Collaborative workspaces that maintain data lineage and access controls: Teams can work together on sensitive data projects while Prophecy maintains comprehensive audit trails and enforces role-based access controls throughout the development process.
- Git-integrated version control for security policy management: All data workflows and their associated security configurations are automatically versioned and stored in enterprise Git repositories, providing the change management and audit capabilities required for regulatory compliance.
- Self-service analytics within governed boundaries: Business analysts can independently access and transform sensitive data while operating within predefined security guardrails that prevent unauthorized data exposure or policy violations.
To transform your enterprise data security posture while enabling true self-service analytics, explore Self-Service Data Preparation Without the Risk and discover how to create secure, collaborative data environments that scale with your business needs.
Ready to give Prophecy a try?
You can create a free account and get full access to all features for 21 days. No credit card needed. Want more of a guided experience? Request a demo and we’ll walk you through how Prophecy can empower your entire data team with low-code ETL today.
Ready to see Prophecy in action?
Request a demo and we’ll walk you through how Prophecy’s AI-powered visual data pipelines and high-quality open source code empowers everyone to speed data transformation
Get started with the Low-code Data Transformation Platform
Meet with us at Gartner Data & Analytics Summit in Orlando March 11-13th. Schedule a live 1:1 demo at booth #600 with our team of low-code experts. Request a demo here.
Related content
A generative AI platform for private enterprise data
Introducing Prophecy Generative AI Platform and Data Copilot
Ready to start a free trial?
Lastest posts

The Future of Data Is Agentic: Key Insights from Our CDO Magazine Webinar

Analytics as a Team Sport: Why Data Is Everyone’s Job Now




